FIR Syslog Integration
timestamp1595890500001
Syslog Integration enables you to export your event data to a syslog server or a security information and events management (SIEM) system. With Syslog Integration, you can store your information and use it for tracking, analysis, and troubleshooting. (also see campus article for details on events supported)
To configure Syslog Integration:
- Click the Settings icon to access the administrative functions.
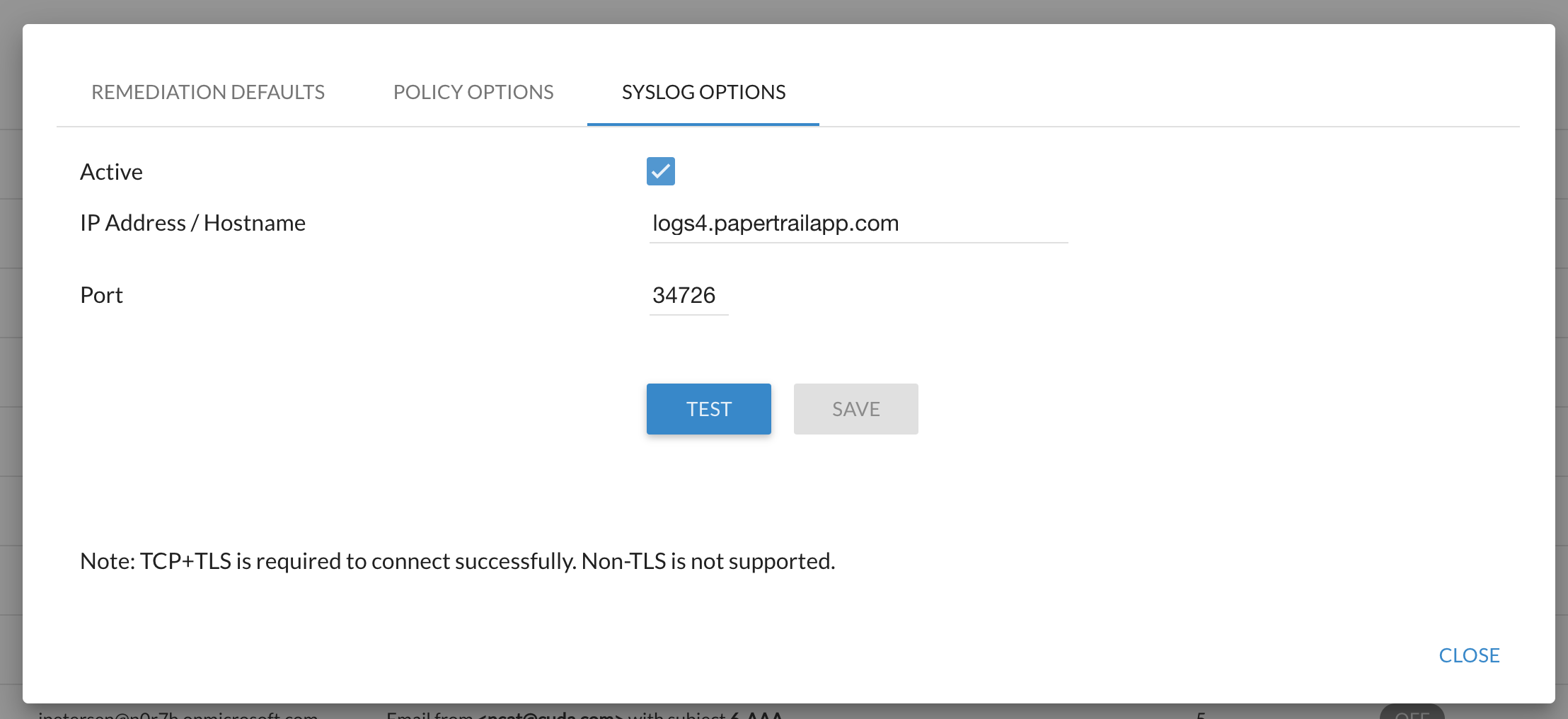
- Select the Syslog Options tab.
- Select the Active checkbox.
- Enter the IP Address/Hostname and Port for your syslog server/SIEM system. The default port is 6514.
- Click Save.
- Click Test to ensure that Barracuda Forensics & Incident Response can connect with your syslog server/SIEM system.
If the test is successful, your message log data begins transferring to your syslog server/SIEM system.
If the test is not successful, check the IP Address/Hostname and Port information and reenter it if needed. Then perform the test again.
To deactivate the syslog server, clear the Active checkbox.
Please Note:
- You can only connect one syslog server/SIEM system at a time. You can delete an existing entry and replace it, but you cannot have multiple entries.
- This feature is available only for Transmission Control Protocol (TCP) with Transport Layer Security (TLS).
- If your syslog server/SIEM system stops responding, data will not spool until the communication is re-established.
- After you enable or disable syslog integration, it can take up to 10 minutes for message transmission to either start or stop.
- Currently only JSON data format is supported. You can parse the data any way you choose to meet the needs of your organization.
Barracuda Forensics and Incident Response sends the following objects to syslog:
- Insights Events
- Remediation Events
(see campus article for details on events supported)